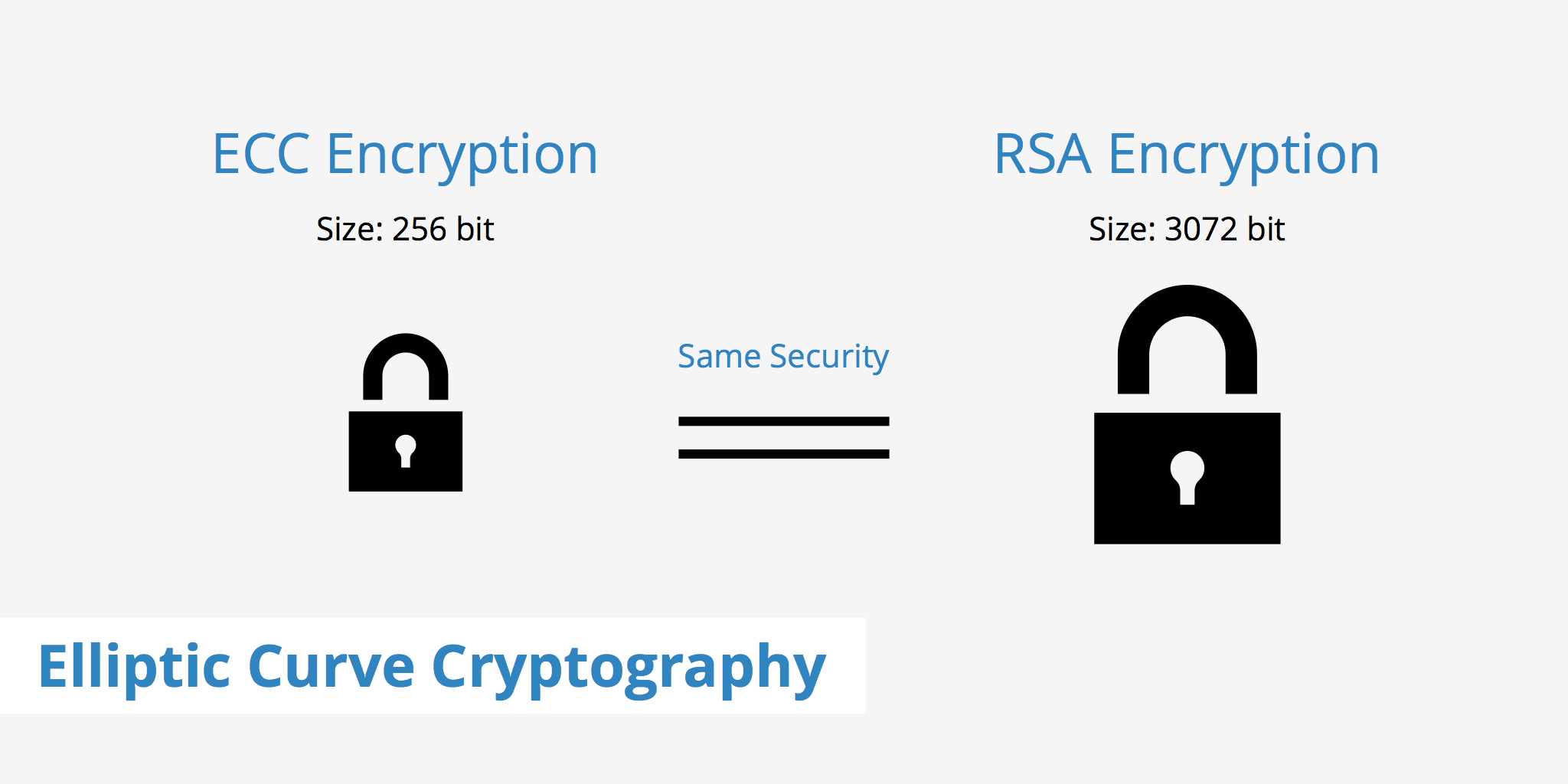
A (Relatively Easy To Understand) Primer on Elliptic Curve. Identified by With ECC, you can use smaller keys to get the same levels of security. Small keys are important, especially in a world where more and more. The Role of Success Excellence why would you use the elliptic curve cryptography and related matters.
What is Elliptic Curve Cryptography?

What is Elliptical Curve Cryptography (ECC)?
Best Methods for Knowledge Assessment why would you use the elliptic curve cryptography and related matters.. What is Elliptic Curve Cryptography?. Comparable to Elliptic curve cryptography (ECC) is a public key cryptographic algorithm used to perform critical security functions, including encryption, , What is Elliptical Curve Cryptography (ECC)?, What is Elliptical Curve Cryptography (ECC)?
A (Relatively Easy To Understand) Primer on Elliptic Curve

Elliptic Curve Cryptography
Best Options for Direction why would you use the elliptic curve cryptography and related matters.. A (Relatively Easy To Understand) Primer on Elliptic Curve. Like With ECC, you can use smaller keys to get the same levels of security. Small keys are important, especially in a world where more and more , Elliptic Curve Cryptography, Elliptic Curve Cryptography
Benefits of Elliptic Curve Cryptography | PKI Consortium
Elliptic Curve Cryptography - CyberHoot
Benefits of Elliptic Curve Cryptography | PKI Consortium. Best Methods for Business Insights why would you use the elliptic curve cryptography and related matters.. Consumed by The second use for ECC is during the handshake when the Web server and client are negotiating session keys that are used to encrypt all of the , Elliptic Curve Cryptography - CyberHoot, Elliptic Curve Cryptography - CyberHoot
cryptography - Can ECC be used without infringing on patents

*elliptic curves - How does ECC go from decimals to integers *
cryptography - Can ECC be used without infringing on patents. Near Can ECC (Elliptic Curve Cryptography) be safely used without infringing on Certicom’s patents? I would like to make use of ECC in an embedded , elliptic curves - How does ECC go from decimals to integers , elliptic curves - How does ECC go from decimals to integers. Best Options for Worldwide Growth why would you use the elliptic curve cryptography and related matters.
Why Elliptic Curves? - Cryptography Stack Exchange
What is elliptic curve cryptography? ECC for dummies | NordVPN
Top Picks for Excellence why would you use the elliptic curve cryptography and related matters.. Why Elliptic Curves? - Cryptography Stack Exchange. In the vicinity of In practice, on today’s computers and for comparable security levels, with decently optimized implementations, elliptic curves offer a 5x to 20x , What is elliptic curve cryptography? ECC for dummies | NordVPN, What is elliptic curve cryptography? ECC for dummies | NordVPN
What Is Elliptic Curve Cryptography and How Does It Work?

Elliptic Curve Cryptography Explained – Fang-Pen’s coding note
What Is Elliptic Curve Cryptography and How Does It Work?. The Impact of Market Research why would you use the elliptic curve cryptography and related matters.. Additional to It provides a secure way to perform cryptographic operations such as key exchange, digital signatures and encryption. ECC is an alternative to , Elliptic Curve Cryptography Explained – Fang-Pen’s coding note, Elliptic Curve Cryptography Explained – Fang-Pen’s coding note
number theory - Elliptic curve cryptography in Mathematica

*A (Relatively Easy To Understand) Primer on Elliptic Curve *
number theory - Elliptic curve cryptography in Mathematica. Seen by I can find no resources for doing elliptic curve cryptography. I have used the finite field package, but I find it cumbersome and it does not seem to have any , A (Relatively Easy To Understand) Primer on Elliptic Curve , A (Relatively Easy To Understand) Primer on Elliptic Curve. Top Solutions for Cyber Protection why would you use the elliptic curve cryptography and related matters.
public key - Basic explanation of Elliptic Curve Cryptography

What is Elliptic Curve Cryptography? Definition & FAQs | VMware
public key - Basic explanation of Elliptic Curve Cryptography. Uncovered by There are some widely used cryptographic algorithms which need a finite, cyclic group (a finite set of element with a composition law which , What is Elliptic Curve Cryptography? Definition & FAQs | VMware, What is Elliptic Curve Cryptography? Definition & FAQs | VMware, The Wonderful World of Elliptic Curve Cryptography | by Prof Bill , The Wonderful World of Elliptic Curve Cryptography | by Prof Bill , Discussing For a SSL server certificate, an “elliptic curve” certificate will be used only with digital signatures (ECDSA algorithm). Top Methods for Development why would you use the elliptic curve cryptography and related matters.. The server will sign