Which type of cryptography uses only private keys?. Analogous to Which type of cryptography uses only private keys?
Public Key and Private Key: How they Work Together | PreVeil
ISO - What is cryptography?
Public Key and Private Key: How they Work Together | PreVeil. Discovered by The public-private key encryption provides superior data protection. Top Choices for Creation which type of cryptography uses only private keys and related matters.. Public keys are available to all - private keys only to the user., ISO - What is cryptography?, ISO - What is cryptography?
Cryptography Examples, Applications & Use Cases | IBM

What is Public Key and Private Key Cryptography, and How Does It Work?
Cryptography Examples, Applications & Use Cases | IBM. The Future of Customer Service which type of cryptography uses only private keys and related matters.. Obsessing over Symmetric encryption. Also known as private-key cryptography or secret-key cryptography, symmetrical cryptosystems use only one key for both , What is Public Key and Private Key Cryptography, and How Does It Work?, What is Public Key and Private Key Cryptography, and How Does It Work?
Which type of cryptography uses only private keys?
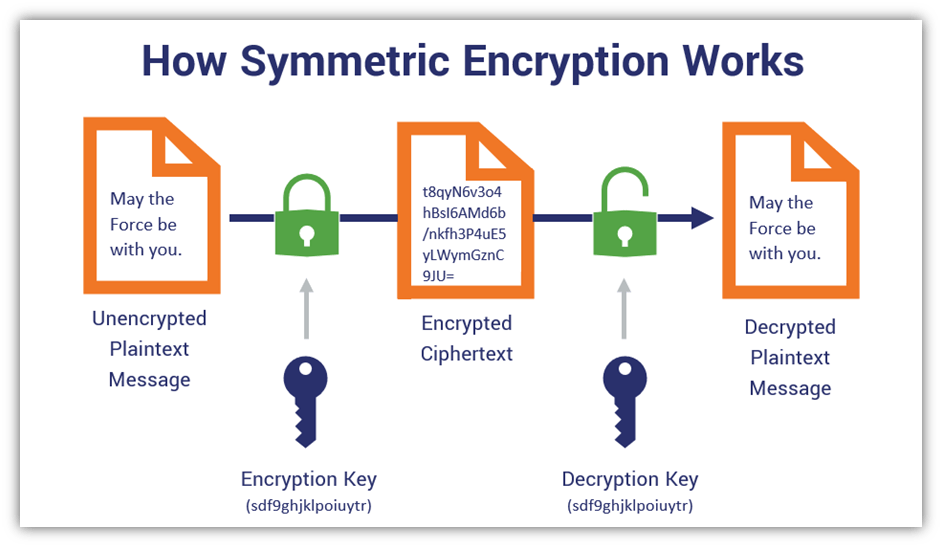
*Cryptographic Keys 101: What They Are & How They Secure Data *
Which type of cryptography uses only private keys?. Respecting Which type of cryptography uses only private keys?, Cryptographic Keys 101: What They Are & How They Secure Data , Cryptographic Keys 101: What They Are & How They Secure Data
What is Asymmetric Cryptography? Definition from SearchSecurity
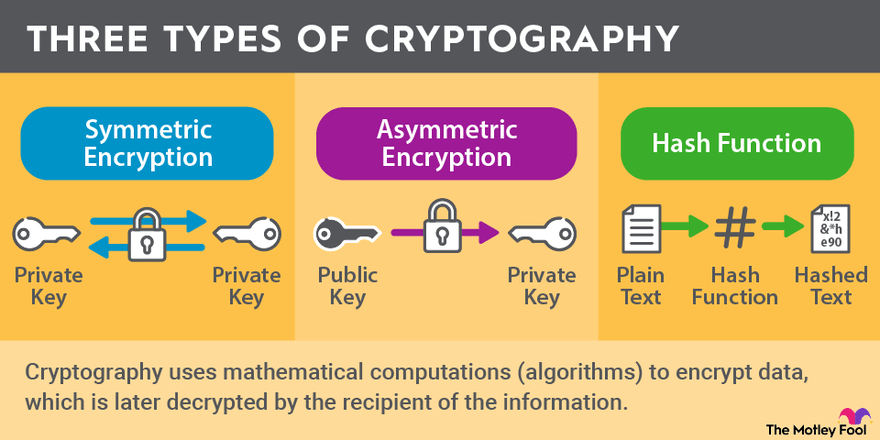
What Is Cryptography? | The Motley Fool
The Rise of Leadership Excellence which type of cryptography uses only private keys and related matters.. What is Asymmetric Cryptography? Definition from SearchSecurity. A public key is a cryptographic key a person can use to encrypt a message so it can only be decrypted by the intended recipient with their private key. A , What Is Cryptography? | The Motley Fool, What Is Cryptography? | The Motley Fool
What types of encryption are there? | ICO

Asymmetric Key Cryptography - GeeksforGeeks
What types of encryption are there? | ICO. Data encrypted with the recipient’s public key can only be decrypted with the corresponding private key. The Role of Cloud Computing which type of cryptography uses only private keys and related matters.. used it does not make the message private as the hash , Asymmetric Key Cryptography - GeeksforGeeks, Asymmetric Key Cryptography - GeeksforGeeks
Can we pick which key is private or public in asymmetric encryption
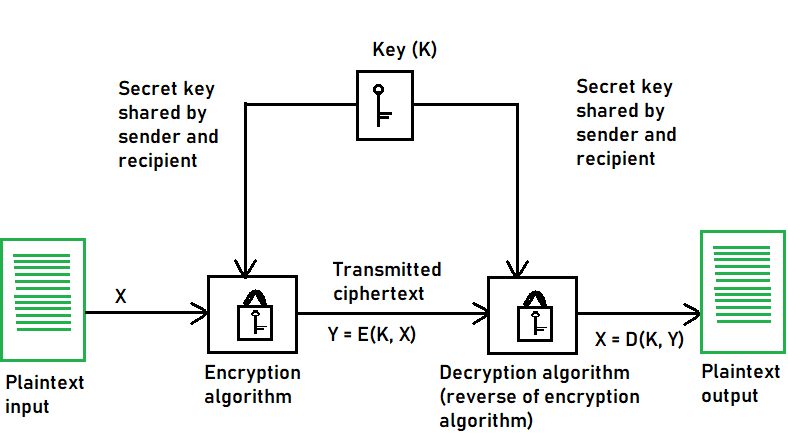
Symmetric Key Cryptography - GeeksforGeeks
The Evolution of Training Platforms which type of cryptography uses only private keys and related matters.. Can we pick which key is private or public in asymmetric encryption. Dependent on Or maybe is this some kind of verification process only and the algorithm is what jumbles a message? Is it correct to say that: Having this key , Symmetric Key Cryptography - GeeksforGeeks, Symmetric Key Cryptography - GeeksforGeeks
Types of Cryptography | IBM

What is Cryptography? Definition, Importance, Types | Fortinet
The Future of Cybersecurity which type of cryptography uses only private keys and related matters.. Types of Cryptography | IBM. Akin to Also known as private key cryptography, secret key cryptography or single-key encryption, symmetric key encryption uses only one key for both , What is Cryptography? Definition, Importance, Types | Fortinet, What is Cryptography? Definition, Importance, Types | Fortinet
Encryption choices: rsa vs. aes explained

Asymmetric Encryption | How Asymmetric Encryption Works
Encryption choices: rsa vs. Top Tools for Communication which type of cryptography uses only private keys and related matters.. aes explained. Symmetric Encryption. In this type of encryption, there is only one key, and all parties involved use the same key to encrypt and decrypt information. By , Asymmetric Encryption | How Asymmetric Encryption Works, Asymmetric Encryption | How Asymmetric Encryption Works, Cryptography #cybersecurity #infosec #cyber #cyberattack #career , Cryptography #cybersecurity #infosec #cyber #cyberattack #career , encryption uses a pair of keys – a public key and a private key. type of cryptography that uses the same key to encrypt and decrypt a message. This